The Lock and Key to Online Safety: Exploring Network Security
Superheroes of the Internet: Keeping Your Network Safe! - TWS Computer Networking Day 4
Introduction:
Hey there, young superheroes of the digital world! Today, we're going to learn about some powerful tools that protect our computer networks from sneaky villains who try to steal our information or cause trouble. Think of these tools as your very own superheroes—Firewalls, Intrusion Detection Systems (IDS), Encryption, Authentication Methods, and Virtual Private Networks (VPNs). So, put on your capes and get ready to explore the exciting world of network security!
Firewalls:
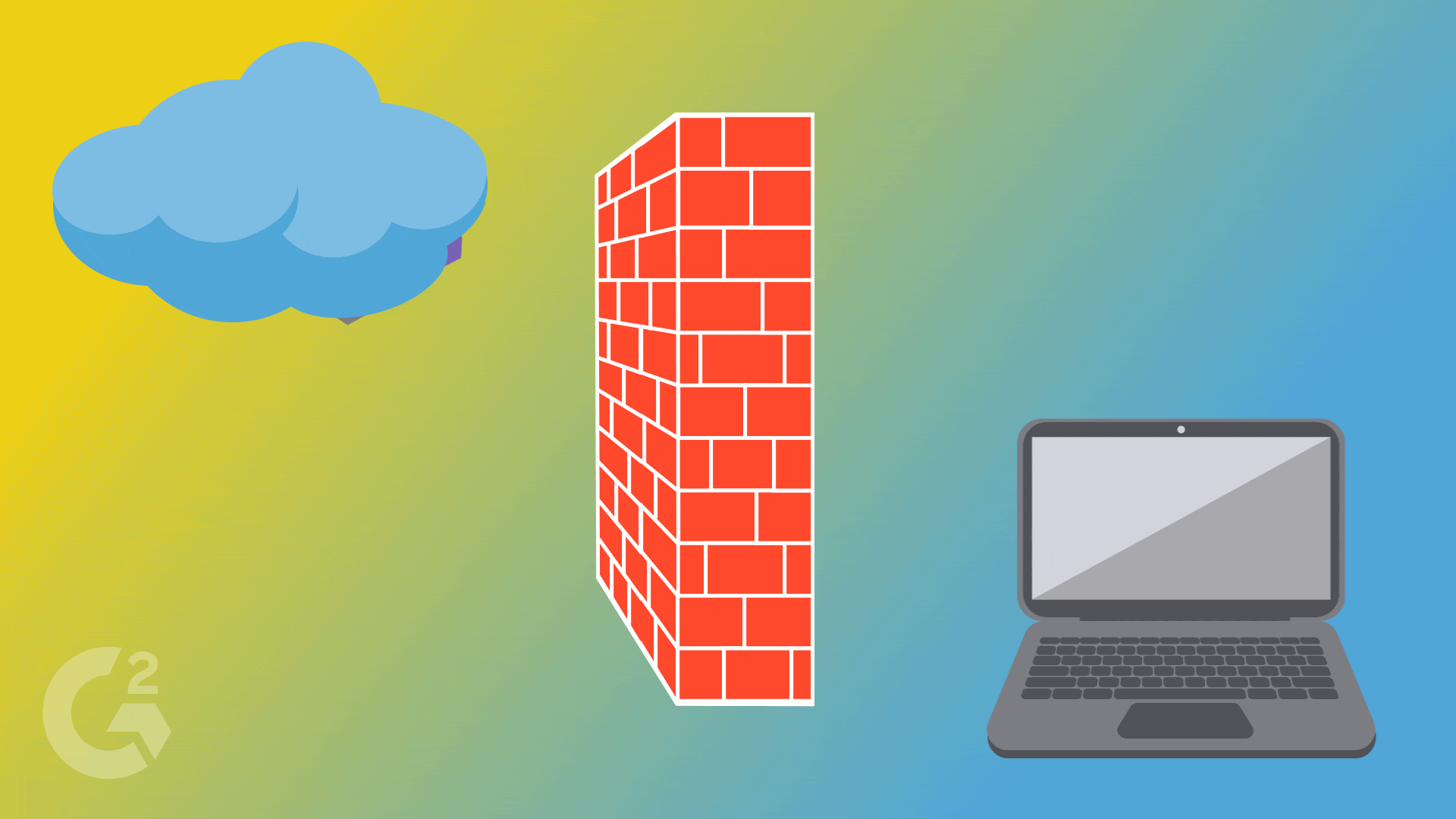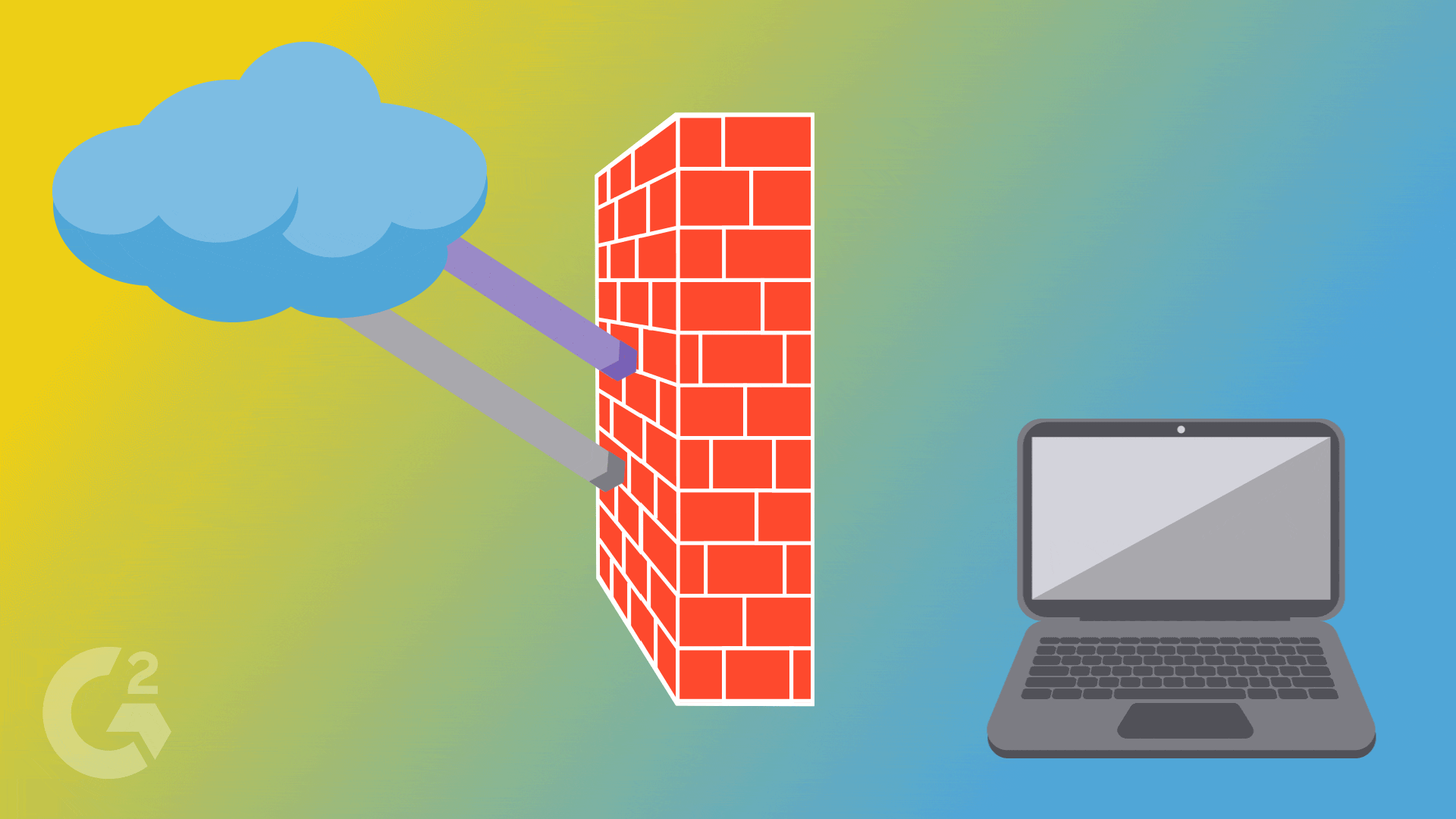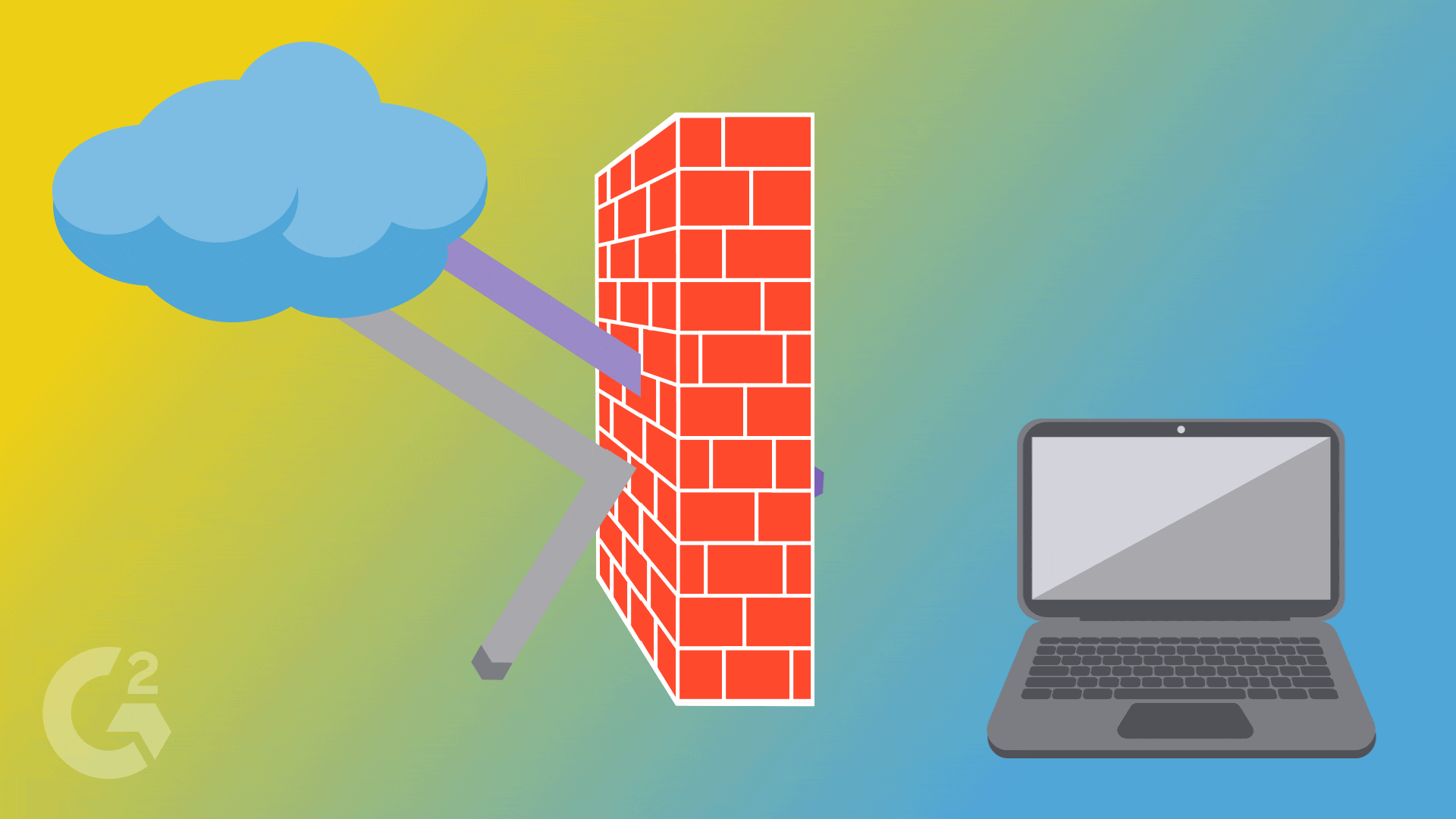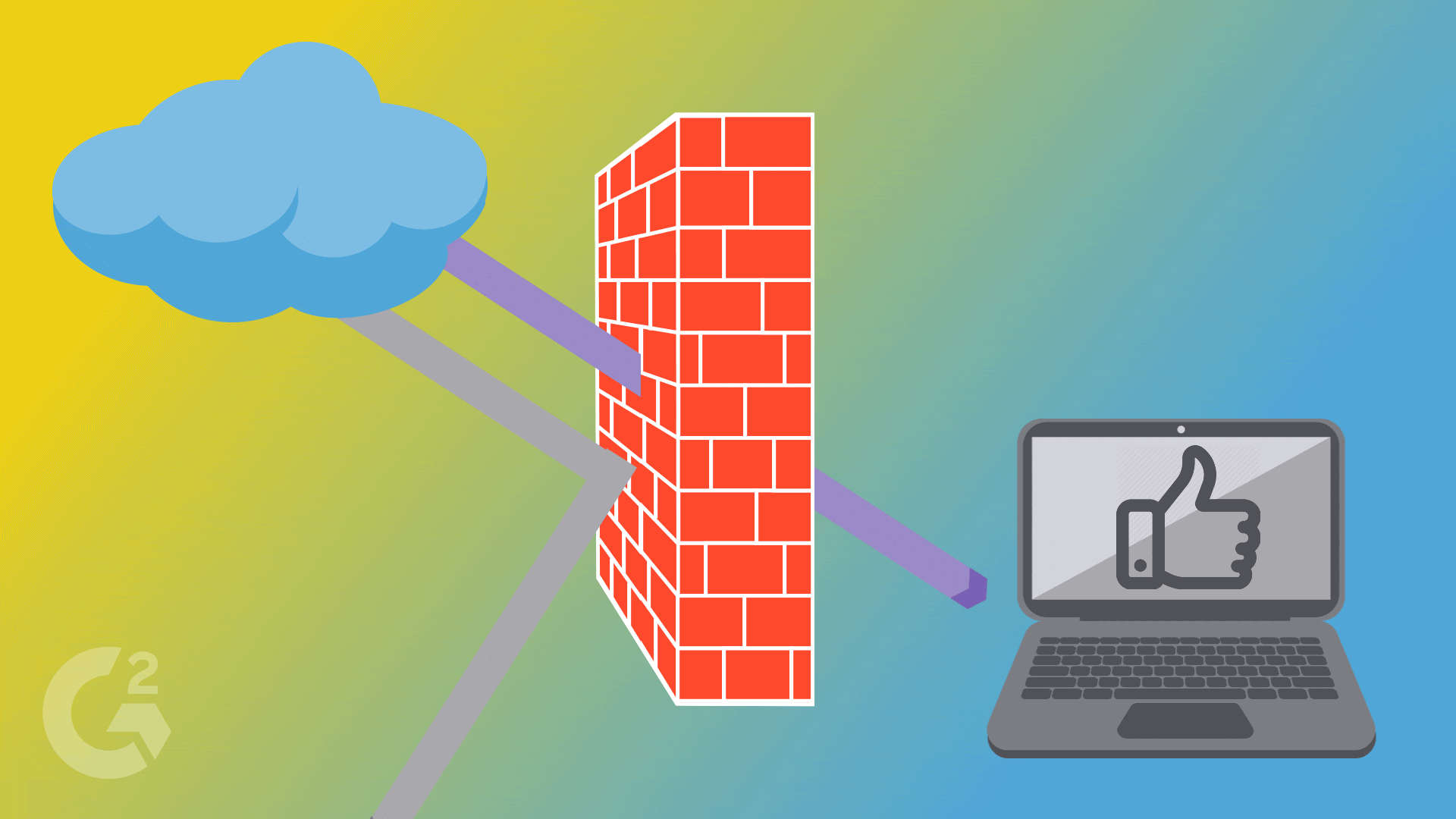
The Shield Protectors 🛡️ Imagine having a protective shield around your home, blocking unwanted guests. That's exactly what a firewall does for our computer networks. It's like a superhero shield that stands between our network and the dangerous outside world. Firewalls check every piece of information trying to enter or leave our network, allowing only the safe and trusted ones to pass through. It keeps the villains out and our network safe!
Intrusion Detection Systems (IDS):

The Watchful Guardians 👀 Just like vigilant guardians, Intrusion Detection Systems keep an eye on our network, watching for any suspicious activity. They scan all the incoming and outgoing traffic, looking for signs of villains trying to break into our network or cause trouble. When an IDS detects something fishy, it raises an alarm, alerting us to take action and thwart the villains' plans. With IDS on our side, we can sleep peacefully knowing our network is guarded!
Encryption and Authentication Methods:

Secret Codes and Handshakes 🤐🤝 Sometimes, we need to send secret messages or sensitive information over the internet. Encryption is like using a secret code to lock our message so that only the intended recipient can decode and understand it. It keeps our secrets safe from prying eyes!
Authentication methods, on the other hand, are like secret handshakes. They ensure that only the right people can access our network or information. Just like superheroes need a special sign to recognize each other, authentication methods verify the identity of users, making sure only authorized individuals can enter.
Virtual Private Networks (VPNs):
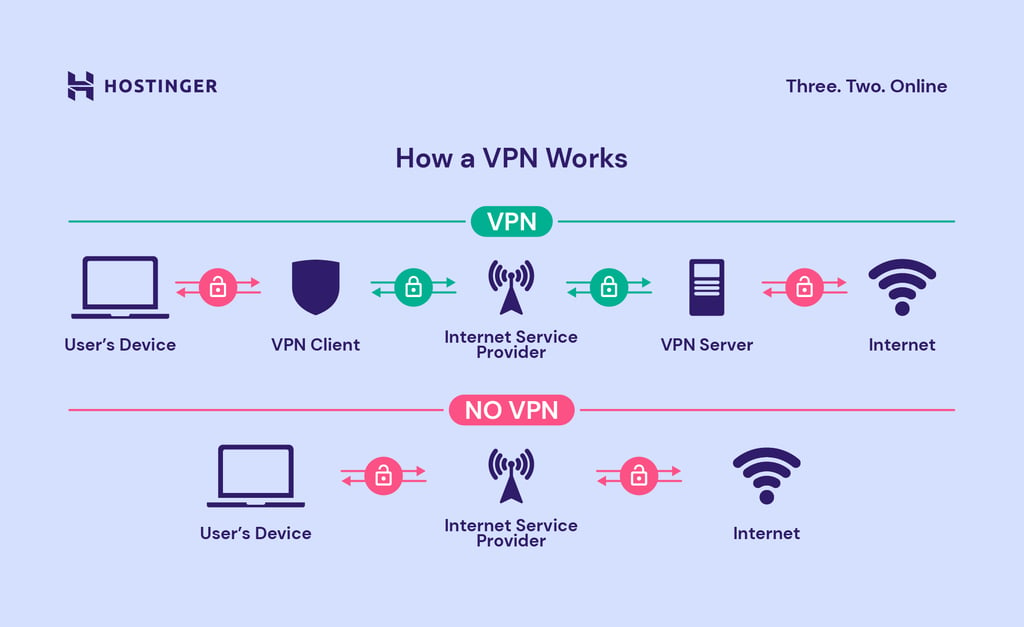
The Invisible Cloak 🧥 Imagine having an invisible cloak that hides you from villains. That's precisely what a Virtual Private Network (VPN) does! It creates a secure tunnel between our device and a remote server, making it seem like we're accessing the internet from a different location. This way, even if villains try to spy on our online activities, they can't see what we're doing. VPNs give us an extra layer of protection, ensuring our privacy and keeping our network hidden from the prying eyes of the bad guys!
Conclusion:
Congratulations, young superheroes! You've learned about some essential tools that keep our computer networks safe and secure. Firewalls, Intrusion Detection Systems, Encryption, Authentication Methods, and Virtual Private Networks work together to protect us from digital villains and ensure our online adventures are safe and enjoyable. So, remember to use these tools wisely and keep your network fortress secure. Stay safe and keep shining bright in the digital world!
